Risk Assessment
The Cyber Risk Assessment Process
A cyber risk assessment is a five-step process that involves meticulously identifying and securing your IT and digital infrastructure against potential threats. This includes:
Curating IT and Digital Assets:
As organisations adopt more technology, assessing all IT assets can be complex. To address this, risk assessments can focus on specific areas like a business unit, location, or department.
Detecting Threats and Vulnerabilities:
This involves identifying suspicious files, unauthorised access attempts, and other unusual activities that could compromise your network security.
Analysing the Risks:
Once you’ve identified threats and vulnerabilities, you need to analyse the associated risks. This involves assessing how likely these vulnerabilities are to be exploited and the potential severity of the impact.
Prioritising Risks:
Prioritising risks based on likelihood of exploitation and potential impact helps you understand your organisation’s overall risk landscape. Tools like a 5×5 risk matrix or a 0-100 grading system can be helpful for this.
Developing a Risk Catalogue:
A risk catalogue tracks security goals, detailing scenarios, dates, controls, and risk levels, with regular reviews for updates and adjustments.
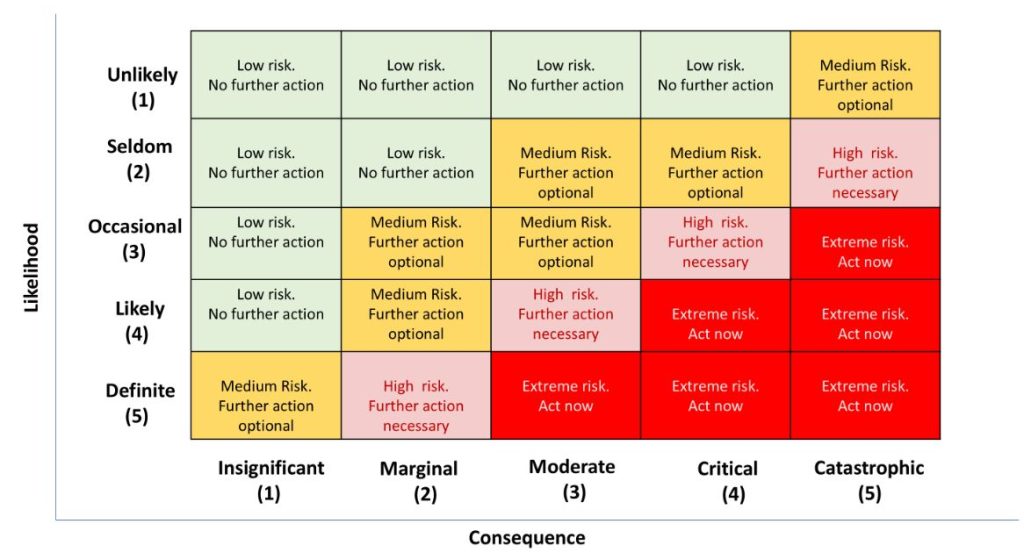
Cyber Security Risk Assessment Matrix
The 5×5 risk assessment matrix has five rows and columns. The columns represent the severity of the risk, and the rows represent the likelihood of it occurring. This creates a grid with 25 cells where risks can be categorised based on their likelihood and severity, ranging from “unlikely and not severe” to “highly likely and severe”.
Cyber Risk Assessment Frameworks
A cyber risk assessment framework outlines an organisation’s approach to identifying, assessing, and managing risks to their IT and digital infrastructure. Organisations can choose to develop their own framework or adopt industry standards like:
- Factor Analysis of Information Risk (FAIR): A quantitative framework for measuring, managing, and communicating information risk.
- OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation): Defines a risk-based strategic assessment technique for security.
- Threat Agent Risk Assessment (TARA): Identifies, assesses, prioritises, and controls cybersecurity risk based on threats.
FAQ's
A cybersecurity risk assessment is the process of analysing your organisation’s IT and digital infrastructure for potential threats. This includes things like laptops, mobiles, and software applications.
Imagine your network as a maze. Cybercriminals look for weak points (vulnerable endpoints) to exploit and reach your sensitive data stored in servers. A cyber risk assessment helps you understand your network’s structure, identifying these vulnerable points and how they connect to critical servers. This information is vital for maintaining a strong security posture. That’s why regular risk assessments are essential.
- New product launches
- Changes to business workflows
- At regular intervals
- To comply with data regulations (e.g. HIPAA requires annual assessments for organisations storing patient data)
The rise of globalisation and the pandemic have expanded the attack surface for cybercriminals, who are using increasingly sophisticated tools and techniques. A data breach can lead to financial losses and irreparable damage to your brand reputation.
Risk assessments can help your organisation achieve:
- Enhanced security posture and resilience
- Real-time defence readiness
- Effective response and mitigation capabilities

